Updating Java
Moderator: Wiz Feinberg
-
Wiz Feinberg

- Posts: 6115
- Joined: 8 Jan 1999 1:01 am
- Location: Mid-Michigan, USA
- State/Province: Michigan
- Country: United States
Since you don't know if you actually need Java, uninstall it and reboot. Once you log back into Windows, start opening programs you use often. Try to open documents, pages, charts, spreadsheets, bedsheets and three sheets to the wind sheets. If nothing fails, Java was not needed.
"Wiz" Feinberg, Moderator SGF Computers Forum
Security Consultant
Twitter: @Wizcrafts
Main web pages: Wiztunes Steel Guitar website | Wiz's Security Blog | My Webmaster Services | Wiz's Security Blog
Security Consultant
Twitter: @Wizcrafts
Main web pages: Wiztunes Steel Guitar website | Wiz's Security Blog | My Webmaster Services | Wiz's Security Blog
-
Mitch Drumm
- Posts: 2663
- Joined: 4 Aug 1998 11:00 pm
- Location: Frostbite Falls, hard by Veronica Lake
- State/Province: -
- Country: United States
That's likely what I'll do at the next aggravation.Wiz Feinberg wrote:Since you don't know if you actually need Java, uninstall it and reboot. Once you log back into Windows, start opening programs you use often. Try to open documents, pages, charts, spreadsheets, bedsheets and three sheets to the wind sheets. If nothing fails, Java was not needed.
Meanwhile: are us ordinary civilians hopelessly locked into the all too frequent Adobe Flash Player update merry-go-round?? No replacement on developer's horizon and pretty much required for typical web surfing? No hope at all unless bad guys decide to exploit something else and why would they do that?
-
Wiz Feinberg

- Posts: 6115
- Joined: 8 Jan 1999 1:01 am
- Location: Mid-Michigan, USA
- State/Province: Michigan
- Country: United States
There are steps you can take to protect your computer from exploit kit attacks.Mitch Drumm wrote: Meanwhile: are us ordinary civilians hopelessly locked into the all too frequent Adobe Flash Player update merry-go-round?? No replacement on developer's horizon and pretty much required for typical web surfing? No hope at all unless bad guys decide to exploit something else and why would they do that?
I already wrote about keeping plugins updated, preferably automatically. Most of them offer that option, along with a set frequency for checking for updates.
Next, select a browser that offers the best user controls over the scripting and plugins it allows to be installed. For me, that is Firefox. Others prefer Google Chrome, Europeans like Opera and I have heard about somebody in the the USA who actually knowingly prefers to use Internet Explorer.
Moving right along, set your configurable browser to "click to play" to run the plugins.
Install the NoScript! Add-on to your Firefox browser. Learn to use it! That responsibility falls on the user, not the author. If you install NoScript and do not learn how to use it, it is similar to obtaining a CCW, buying a good handgun, but never learning to fire it.
NoScript protects against any scripted silent redirects, Java exploits, Flash exploits and other scripted attacks. It also protects against Facebook Clickjacking scams and other malicious overlays.
Keep up to date with operating system updates, whether Windows, Mac or Linux. If you have Office programs, accept updates as they are offered. Many email-borne attacks use Macro scripts, VBS, or other scripting tricks to infect computers when the attachment is opened.
Along the same line, if you have a PDF reader, set it to check for updates regularly and install them automatically. Adobe Reader is the primary target for PDF attachment attacks. Keep it updated and apply the recommended security settings.
Install the best anti-malware and/or anti-virus protection you can afford. Resubscribe annually if you are satisfied. Try another brand if you feel it let you down. I use Trend Micro Internet Security and stand by it.
Look into what level of permissions your user account has on your computer. It should not be Administrator. If you have been operating as the Administrator, you are 92% more likely to have the computer taken over silently by an exploit kit than a limited or standard user account. Plus, the damage that can be inflicted by a drive-by download attack on an Administrator account is far beyond that inflicted on a Standard User.
If your email client offers spam filters, learn to apply them. If it allows you to write your own filters, learn to write them. Otherwise, be suspicious of unexpected email attachments from senders you don't really know or haven't initiated a conversation with. If your anti-virus program offers a plug-in for email, apply it.
Beware of clicking on links in sensational posts on Facebook, or other social networks. The more sensational the wording and any images in it, the more danger could be lurking at the end of the link.
Do not allow yourself to be tricked into opening suspicious attachments, or clicking on links in poorly written email messages, or private messages. If the grammar is poor in your own language, it may have been composed in Russia, Spain, Nigeria, or The Ukraine.
Don't respond to work at home solicitations as 99.9999999% are for money mules for funds pilfered from bank accounts by Trojan Horse programs, or other trickery. Money mules can go to jail if convicted. The usual charge is Money Laundering, prosecuted under the RICO Act.
"Wiz" Feinberg, Moderator SGF Computers Forum
Security Consultant
Twitter: @Wizcrafts
Main web pages: Wiztunes Steel Guitar website | Wiz's Security Blog | My Webmaster Services | Wiz's Security Blog
Security Consultant
Twitter: @Wizcrafts
Main web pages: Wiztunes Steel Guitar website | Wiz's Security Blog | My Webmaster Services | Wiz's Security Blog
-
Mitch Drumm
- Posts: 2663
- Joined: 4 Aug 1998 11:00 pm
- Location: Frostbite Falls, hard by Veronica Lake
- State/Province: -
- Country: United States
Thanks Wiz. I'll mull all of that over and try to apply some time to those areas where I'm not up to snuff--mainly on proper use of NoScript---which I've had for several years but have not seriously examined.
For one thing, I'm not entirely clear on how eager I should be to Whitelist ANYBODY, exploiters being what they are. "Click to play" type stuff seems to eventually just become something you inevitably OK whenever it pops up.
Otherwise, I guess I'll just pray for HTML 5 and the death of Adobe and maybe Oracle too, but I suspect that will be a long wait.
For one thing, I'm not entirely clear on how eager I should be to Whitelist ANYBODY, exploiters being what they are. "Click to play" type stuff seems to eventually just become something you inevitably OK whenever it pops up.
Otherwise, I guess I'll just pray for HTML 5 and the death of Adobe and maybe Oracle too, but I suspect that will be a long wait.
-
Wiz Feinberg

- Posts: 6115
- Joined: 8 Jan 1999 1:01 am
- Location: Mid-Michigan, USA
- State/Province: Michigan
- Country: United States
Big companies have paid webmasters who analyze access logs for gaining insight into what technologies, operating systems and browsers are being used. Visitors who land on a page, after clicking a referrer link, then bail after a couple of seconds are usually looked at closely. The analyzer scripts reveal when a browser fails to load various scripts. If JavaScript, Flash, Java, Shockwave, Silverlight, ActiveX, or any other resource that is supposed to load isn't called at all, that browser is either blocking them, or cannot use those files. They will see this and eventually, will drop those technologies in favor of something else that works in most browsers and leads to conversions and sales.
"Wiz" Feinberg, Moderator SGF Computers Forum
Security Consultant
Twitter: @Wizcrafts
Main web pages: Wiztunes Steel Guitar website | Wiz's Security Blog | My Webmaster Services | Wiz's Security Blog
Security Consultant
Twitter: @Wizcrafts
Main web pages: Wiztunes Steel Guitar website | Wiz's Security Blog | My Webmaster Services | Wiz's Security Blog
-
Brint Hannay
- Posts: 3960
- Joined: 23 Dec 2005 1:01 am
- Location: Maryland, USA
- State/Province: Maryland
- Country: United States
Any tips on how best to use NoScript?
I have it, but essentially only "Temporarily Allow" the specific item at the top of the list (the one I was actually trying to open), no matter how much I think it can be trusted, and only any others that I can recognize as being relevant, as for example a subset (forgive the inaccurate term) of the main item.
I only open the NoScript list if something on the web page isn't working. It's a nuisance when the sometimes amazingly long list has to be scrutinized, but it seems a small price to pay for security.
One thing I never "Allow" is "Google analytics". Maybe I'm paranoid, but I see no reason to consciously let Google track me.
I have it, but essentially only "Temporarily Allow" the specific item at the top of the list (the one I was actually trying to open), no matter how much I think it can be trusted, and only any others that I can recognize as being relevant, as for example a subset (forgive the inaccurate term) of the main item.
I only open the NoScript list if something on the web page isn't working. It's a nuisance when the sometimes amazingly long list has to be scrutinized, but it seems a small price to pay for security.
One thing I never "Allow" is "Google analytics". Maybe I'm paranoid, but I see no reason to consciously let Google track me.
-
Wiz Feinberg

- Posts: 6115
- Joined: 8 Jan 1999 1:01 am
- Location: Mid-Michigan, USA
- State/Province: Michigan
- Country: United States
Aside from reading all the instructions on the NoScript! home page, this is the skinny.Brint Hannay wrote:Any tips on how best to use NoScript?
I have it, but essentially only "Temporarily Allow" the specific item at the top of the list (the one I was actually trying to open), no matter how much I think it can be trusted, and only any others that I can recognize as being relevant, as for example a subset (forgive the inaccurate term) of the main item.
I only open the NoScript list if something on the web page isn't working. It's a nuisance when the sometimes amazingly long list has to be scrutinized, but it seems a small price to pay for security.
One thing I never "Allow" is "Google analytics". Maybe I'm paranoid, but I see no reason to consciously let Google track me.
If you see a red mark, or red slash in a circle in the NoScript! icon, it means that either included scripts or the website itself is being blocked (for your protection). If you hover your mouse pointer over the icon a flyout menu will appear and detail everything that is allowed or blocked. If you look at the blocked items, shown in total red circles and slashes, you will know if they are local or third party. There is a section for Recently Blocked websites and another for Untrusted ones.
I understand that the notation used in the flyout display can confuse some people. That is because it appears to be written in RPN logic. When the Status text says "Allow" - and the icon has the plain blue S in a white circle, all scripting, if any is present, is allowed on that page. If the icon has a red circle and slash, scripting is denied, and the text says "Forbid." Clicking on those lines reverses the status for that resource.
This means that clicking on the status text Allow actual forbids it. That is why I don't like RPN language. I first encountered this aberration in a hand held programmable calculator mage by Hewlett Packard. Every term was entered in reverse to what I regarded as normal thinking.
If you basically trust the website itself, Allow scripting for that website. If you don't specifically trust the included sources (outside scripts, ad networks, metrics analyzers), leave them as Forbid, with red circles and slashes. If you visit a site that you think has been compromised by hackers, add it to Untrusted. You can still view plain text and most images, but no scripts will run. This blocks exploit kits.
I hope this helps. Again, read the detailed instructions on the NoScript! homepage.
I can tell you with certainty that I browse the Interwebs with Firefox and always use the NoScript! Add-on, to which I occasionally make a donation. I have investigated known or suspected malicious or scam, or phishing web pages using it and have not been compromised yet. Sometimes, I have to override Trend Micro protection to see that content as HTML. Other times, I may choose to look at the page's actual source code, in safe plain text, using Wannabrowser.
"Wiz" Feinberg, Moderator SGF Computers Forum
Security Consultant
Twitter: @Wizcrafts
Main web pages: Wiztunes Steel Guitar website | Wiz's Security Blog | My Webmaster Services | Wiz's Security Blog
Security Consultant
Twitter: @Wizcrafts
Main web pages: Wiztunes Steel Guitar website | Wiz's Security Blog | My Webmaster Services | Wiz's Security Blog
-
Wiz Feinberg

- Posts: 6115
- Joined: 8 Jan 1999 1:01 am
- Location: Mid-Michigan, USA
- State/Province: Michigan
- Country: United States
As added info, a smart webmaster can use NoScript! to detect a compromise on a website he is or was involved with. If you have coded everything properly, there shouldn't be any blocked resources, other than maybe from an ad network (if you run Google or other third party included ads).
Say you made a website that has no imported ads, just your own benign same origin scripts. Everything is on the up and up and NoScript! said all clear after you tested it. Say you visit that website some time later and see a partial red icon for NoScript. Hover over the icon and see what is being blocked. It may be a URL, or an IP address, or some file you don't recognize. NoScript! may have revealed the presence of a hack. If you are a competent webmaster, you already know how to investigate the source code. The cleanup may not be as easy though.
Say you made a website that has no imported ads, just your own benign same origin scripts. Everything is on the up and up and NoScript! said all clear after you tested it. Say you visit that website some time later and see a partial red icon for NoScript. Hover over the icon and see what is being blocked. It may be a URL, or an IP address, or some file you don't recognize. NoScript! may have revealed the presence of a hack. If you are a competent webmaster, you already know how to investigate the source code. The cleanup may not be as easy though.
"Wiz" Feinberg, Moderator SGF Computers Forum
Security Consultant
Twitter: @Wizcrafts
Main web pages: Wiztunes Steel Guitar website | Wiz's Security Blog | My Webmaster Services | Wiz's Security Blog
Security Consultant
Twitter: @Wizcrafts
Main web pages: Wiztunes Steel Guitar website | Wiz's Security Blog | My Webmaster Services | Wiz's Security Blog
-
Charlie McDonald

- Posts: 11066
- Joined: 17 Feb 2005 1:01 am
- Location: out of the blue
- State/Province: -
- Country: United States
This is a real education.
Now that everyone has helped me solve my problems both personal and scientific... this may be a bit off topic, but not unrelated,
concerning the peaceful takeover of my Chrome by AVG. Ugly is in the eye of the beholder, but you know Leslie Neilsen.
It does give one a feeling of security, but it doesn't give the usual shortcuts to the bank; you wade thru links to get there.
Thanks to the forum's Earnest Bovine I can take pictures.

When it first made the change, it gave the prompt you see in a previous post, allowing you to change it back in settings.
In the upper right of the screen shot, it says 'Restore default in new tab.' In settings it gives several options:
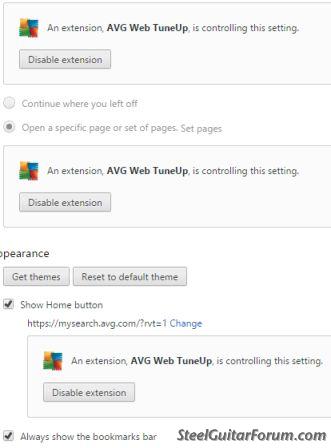
I think it's all fine. What I'm wondering if I, under appearance, I reset default or go to the Chrome Store (what a virtual laugh ) and put up, say, New York City at Night if I will disable the entire Chrome Web Tuneup. It's fine to have it, but I liked the way my browser knew almost telepathically where I wanted to go, and it would take me straight away to Gmail, the Forum, or to the bank. I don't care about the porn. Particularly since Flash is in the pan. If I 'get themes,' will the AVG unit still be active, or V-ger? Or take all my base?
) and put up, say, New York City at Night if I will disable the entire Chrome Web Tuneup. It's fine to have it, but I liked the way my browser knew almost telepathically where I wanted to go, and it would take me straight away to Gmail, the Forum, or to the bank. I don't care about the porn. Particularly since Flash is in the pan. If I 'get themes,' will the AVG unit still be active, or V-ger? Or take all my base?
Now that everyone has helped me solve my problems both personal and scientific... this may be a bit off topic, but not unrelated,
concerning the peaceful takeover of my Chrome by AVG. Ugly is in the eye of the beholder, but you know Leslie Neilsen.
It does give one a feeling of security, but it doesn't give the usual shortcuts to the bank; you wade thru links to get there.
Thanks to the forum's Earnest Bovine I can take pictures.

When it first made the change, it gave the prompt you see in a previous post, allowing you to change it back in settings.
In the upper right of the screen shot, it says 'Restore default in new tab.' In settings it gives several options:

I think it's all fine. What I'm wondering if I, under appearance, I reset default or go to the Chrome Store (what a virtual laugh
-
Brint Hannay
- Posts: 3960
- Joined: 23 Dec 2005 1:01 am
- Location: Maryland, USA
- State/Province: Maryland
- Country: United States
This sounds opposite to how I've been understanding the flyout list. When a page on the flyout list has the red circle and slash, it says "Forbid" for that page--meaning, as I take it, that I am offered the option to Forbid, and scripts are in fact currently allowed for that page.I understand that the notation used in the flyout display can confuse some people. That is because it appears to be written in RPN logic. When the Status text says "Allow" - and the icon has the plain blue S in a white circle, all scripting, if any is present, is allowed on that page. If the icon has a red circle and slash, scripting is denied, and the text says "Forbid." Clicking on those lines reverses the status for that resource.
For example, right now I'm on the Forum. In the corner of the page is the blue S with no red circle/slash at all. I take this to mean that scripts are allowed for the Forum (one of the only pages that I have (I think!) granted non-temporary permission). When I put my cursor on the NoScript icon, the flyout list, by contrast, shows the red circle/slash next to the Forum, with "Forbid".
It would make more sense to me if the icon next to a page on the flyout list would show the current status, and the text should offer to change to a different status from the status the icon shows.
Have I got this all wrong, and all along I've been forbidding what I want to allow and vice versa??:eek:
-
Charlie McDonald

- Posts: 11066
- Joined: 17 Feb 2005 1:01 am
- Location: out of the blue
- State/Province: -
- Country: United States
New topic?
Wiz, I hope they pay you handsomely in Beta Centauri Star Credits. I'm enjoying reading other people's problems and
their capable solutions.
If you like, you can make my post a new topic and we'll sit on it; I'm not going anywhere and neither is Chrome,
and I have a new evolutionary copediment I'm working on.
I get a good education here, really.
Back to Java and Applets for breakfast. Mmmm.
their capable solutions.
If you like, you can make my post a new topic and we'll sit on it; I'm not going anywhere and neither is Chrome,
and I have a new evolutionary copediment I'm working on.
I get a good education here, really.
Back to Java and Applets for breakfast. Mmmm.
-
Mitch Drumm
- Posts: 2663
- Joined: 4 Aug 1998 11:00 pm
- Location: Frostbite Falls, hard by Veronica Lake
- State/Province: -
- Country: United States
I'm with Brint. More confusion.Brint Hannay wrote:This sounds opposite to how I've been understanding the flyout list.I understand that the notation used in the flyout display can confuse some people. That is because it appears to be written in RPN logic. When the Status text says "Allow" - and the icon has the plain blue S in a white circle, all scripting, if any is present, is allowed on that page. If the icon has a red circle and slash, scripting is denied, and the text says "Forbid." Clicking on those lines reverses the status for that resource.
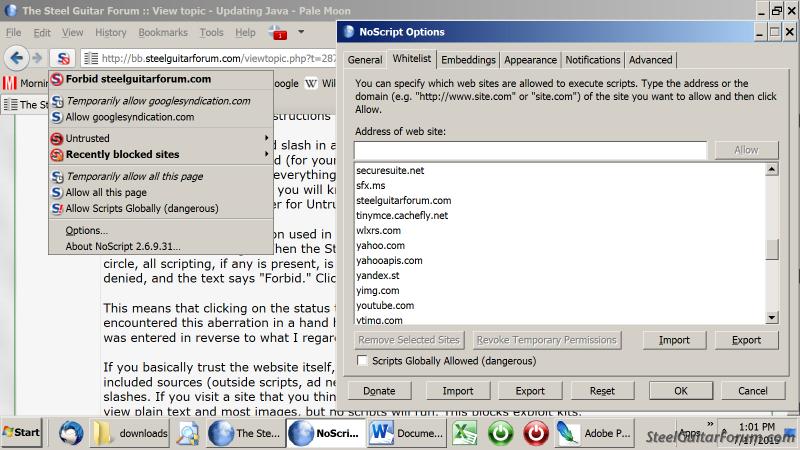
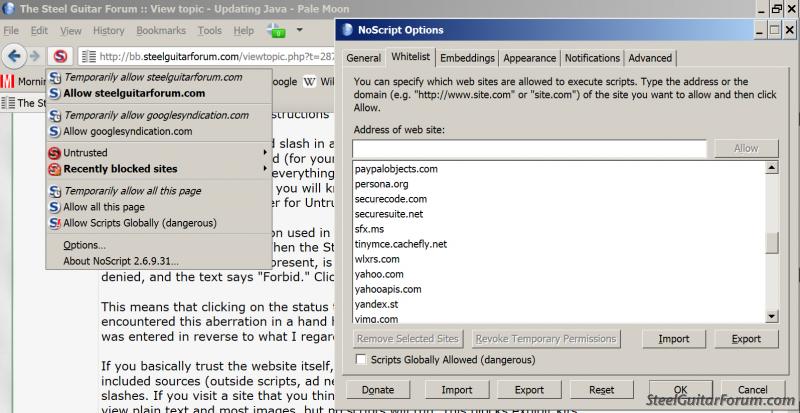
Attached are two screen shots I just took. In the first, "Allow" has already been clicked for the Steel forum, Forbid is now shown, and the Steel forum appears on the whitelist. In the second, the flyout text says "allow" for the Steel forum, but allow has NOT yet been clicked and the Steel forum does NOT appear in the whitelist.
Maybe "whitelist" means "blacklist" in RPN.
-
Charlie McDonald

- Posts: 11066
- Joined: 17 Feb 2005 1:01 am
- Location: out of the blue
- State/Province: -
- Country: United States
Wiz, and others, I withdraw my question and non-problem without prejudice for my previous post though off topic. How about those Dodgers?!
In the spirit of things, as it appears we're all at the learning stage of these new things as they arise and always will,
I took it upon myself to disable the appearance and selected themes and all the AVG options disappered from Settings.
Yet.. something new. There are 'puzzle piece' here and there with 'Right click to view.' Sometimes it's an ad, sometimes a link
to a PDF reader for something I just searched for. If it's a flash player, it says so and seems to enable Flash one time.
It may be that AVG left some security features behind and the intended benefit might still be enabled, and back are my quick links
to Gmail, the Forum, and don't forget the bank, saving precious seconds for the busy time traveler in the modern world.
However it is or was, a satisfactory ending, because the feature didn't offer much. My browser now remembers where I was a minute ago,
doesn't offer me Facebook and Tweeter or CNBC, and I can once again see New York at Night or even glimpse the Crack In Time And Space.
My base are safe!
In the spirit of things, as it appears we're all at the learning stage of these new things as they arise and always will,
I took it upon myself to disable the appearance and selected themes and all the AVG options disappered from Settings.
Yet.. something new. There are 'puzzle piece' here and there with 'Right click to view.' Sometimes it's an ad, sometimes a link
to a PDF reader for something I just searched for. If it's a flash player, it says so and seems to enable Flash one time.
It may be that AVG left some security features behind and the intended benefit might still be enabled, and back are my quick links
to Gmail, the Forum, and don't forget the bank, saving precious seconds for the busy time traveler in the modern world.
However it is or was, a satisfactory ending, because the feature didn't offer much. My browser now remembers where I was a minute ago,
doesn't offer me Facebook and Tweeter or CNBC, and I can once again see New York at Night or even glimpse the Crack In Time And Space.
My base are safe!
-
Dave Potter
- Posts: 1567
- Joined: 15 Apr 2003 12:01 am
- Location: Texas
- State/Province: Texas
- Country: United States
I used to pay for anti-virus/anti-malware software - did it for years. Past few years, though, I quit all that, using instead just the free Microsoft Security Essentials and Windows Firewall, also free. Far as I can tell, they're working...I have no "puzzle pieces" nor any other unexpected things happening, and the price is right.
Of course, I also browse with Firefox, enhanced with YesScript, Blur, AdBlock Plus, and Flash Control. Works for me. That combination breaks functionality on a few web sites I frequent, but disabling them is quick and easy.
Of course, I also browse with Firefox, enhanced with YesScript, Blur, AdBlock Plus, and Flash Control. Works for me. That combination breaks functionality on a few web sites I frequent, but disabling them is quick and easy.
-
Charlie McDonald

- Posts: 11066
- Joined: 17 Feb 2005 1:01 am
- Location: out of the blue
- State/Province: -
- Country: United States
-
Dave Potter
- Posts: 1567
- Joined: 15 Apr 2003 12:01 am
- Location: Texas
- State/Province: Texas
- Country: United States
Thanks, Charlie. There are more knowledgeable people here, Wiz and Jack among them, and I try to learn from them. And the usual disclaimer applies: You gotta' use judgement about what you click on, what you download, and what you allow to "run" (.exe files, etc). It's a jungle out there.Charlie McDonald wrote:I'm glad to be learning through this thread. Your experience helps a lot, Dave.